Learn the Cyber Security Education Project to familiarize users with not just the basics but all aspects of working in the field of cybersecurity. They have at their disposal examples of violations, ways to protect against them, real cases and their results, options for dealing with crises and exiting them, as well as a list of global laws that regulate and define these actions.
The graduate courses provide the student with a set of knowledge that will be useful in the future to build a career in a structure that protects against all types of cybercrime.
FEATURES OF LEARN CYBER SECURITY APK
FUNDAMENTAL OF INFORMATION SECURITY
The basis of information security is the basic principles and activities that ensure the protection of confidential information, the integrity, confidentiality, and availability of information. These principles cover many aspects such as risk management, access control, encryption, and security policies. Risk management involves identifying potential threats and vulnerabilities, assessing their potential impact, and implementing measures to reduce or eliminate these risks. Access control ensures that only authorized individuals have appropriate levels of access to information systems and data.
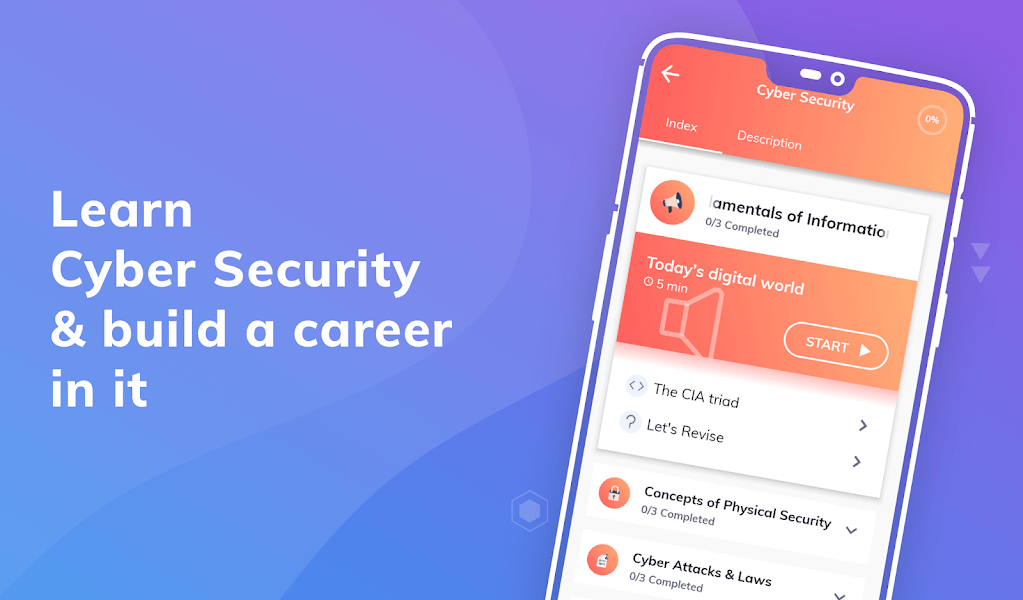
Encryption plays an important role in security by converting data into a format that cannot be read without a decryption key. In addition, well-defined security policies guide organizations in establishing and maintaining a secure environment, incident response procedures, employee training, and regular security assessments. A holistic understanding of these fundamental principles is essential for organizations to develop a robust approach to information security in an increasingly interconnected and digital world.
CYBER ATTACKS & CYBER LAWS
Cyber attacks and cyber law represent two interdependent aspects of the complex environment of the digital age. From malware and phishing to more sophisticated forms such as ransomware and advanced persistent threats, cyber-attacks pose a significant threat to individuals, businesses, and governments. These attacks typically exploit vulnerabilities in computer systems and networks to gain unauthorized access, steal information, or disrupt critical operations. Due to the growing threat of cyber attacks, cyber laws have been developed to create a legal framework to deter and prevent this type of malicious activity.
These laws define the crimes, punishments, and responsibilities of both individuals and organizations involved in cybercrime. They also deal with issues related to digital privacy, intellectual property, and data protection. The evolving nature of cyber threats requires constant innovation and international cooperation to adapt to the dynamic nature of the digital environment and create an effective cyber law that forms the legal basis for combating cybercrime globally.
DIGITAL FORENSICS
Digital forensics is a specialized field of cybersecurity that involves the study, analysis, and recovery of digital evidence to detect and understand cybercrimes and security breaches. In an increasingly interconnected world, digital forensics plays an important role in identifying, storing, and examining electronic data for legal purposes. This process involves a thorough examination of computer systems, networks, and digital devices to determine the origin of a cyber attack, gather evidence, and recover digital activity.
Digital forensics professionals use a variety of tools and techniques to recover deleted files, analyze network traffic, and detect patterns of malicious activity. Digital forensics research findings are vital to assisting law enforcement agencies, businesses, and individuals in responding to and recovering from cyber incidents, as well as supporting legal proceedings. As technology evolves, the field of digital forensics keeps pace with new challenges and ensures effectiveness in addressing the complex and dynamic nature of cyber threats.

















